In this series of three posts, I demonstrate the installation and configuration of Microsoft’s Local Administrator Password Solution (LAPS). This is the third and final post that covers the group policy configuration of LAPS, as well as a brief demonstration. For links to parts 1 and 2, see the bottom of this post.
Configuring Group Policy
We’ve got the software installed, and AD configured, all that’s left is to turn the thing on! Fortunately there’s an ADM file included with the management tools, so this is pretty straightforward. Open GPMC and edit the LAPS policy we created earlier. If you’d prefer, you can create a separate policy for configuration. Either way, open Group Policy Editor and navigate to Policies -> Administrative Templates -> LAPS. 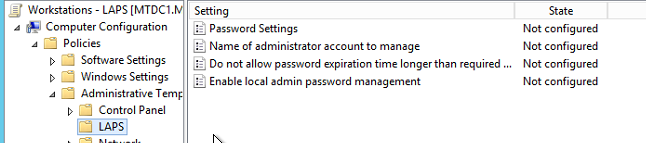 These settings are pretty straightforward, so configure them how you like. I’ve configured mine like so:
These settings are pretty straightforward, so configure them how you like. I’ve configured mine like so:
- Enable local admin password management: Enabled
- Password Settings: Enabled
- Complexity: Large letters, small letters, numbers, specials
- Length: 14 characters
- Age: 30 days
- Name of administrator account to manage: Not Configured (this will use the default SID -500 account)
- Do not allow password expiration time longer than required by policy: Enabled
Congratulations, you’re done! It’s as easy as that!
Using LAPS
There’s two ways to retrieve a computer’s password from Active Directory. ## The Hard Way Every computer updates its AD attributes, so surely Attribute Editor would be a good place to start? Crank up Users and Computers and browse to the computer. You’ll see the admin password and (unintelligible) password expiry time: 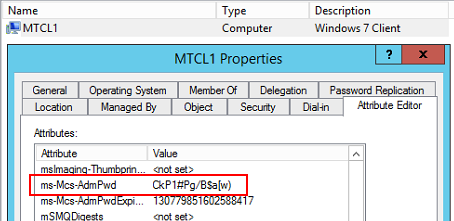 ## The Easy Way Remember right back in part 1 we had the option to install a fat client? Now’s the time to check that out. You’ll see an app called LAPS UI pinned to your start screen. Run it as administrator and you’ll see a fairly basic user interface. Enter a computer’s name and hit the Search button to retrieve the computer’s password and a readable expiry time.
## The Easy Way Remember right back in part 1 we had the option to install a fat client? Now’s the time to check that out. You’ll see an app called LAPS UI pinned to your start screen. Run it as administrator and you’ll see a fairly basic user interface. Enter a computer’s name and hit the Search button to retrieve the computer’s password and a readable expiry time. 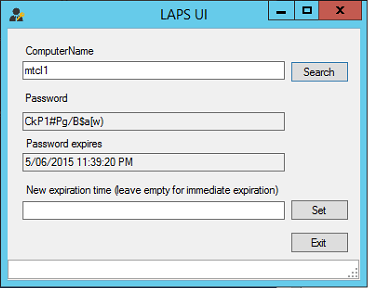
As an aside, /u/accountnumber3 on reddit offers this programmatic solution to retrieving the password. This would be very useful if you wish to retrieve these values using a script or other unattended solution:
Get-ADComputer MTCL1 -Properties ms-Mcs-AdmPwd | select name, ms-Mcs-AdmPwdWell, that’s that! There’s not much more to do. If you want to add more OUs or security groups in future, just run through the relevant steps again. This is a really great tool that’s very simple to deploy, and it can increase your AD security exponentially. Thanks for reading!
What Else?
Comments/questions
There's no commenting functionality here. If you'd like to comment, please either mention me (@[email protected]) on Mastodon or email me. I don't have any logging or analytics running on this website, so if you found something useful or interesting it would mean a lot to hear from you.