In this series of three posts, I demonstrate the installation and configuration of Microsoft’s Local Administrator Password Solution (LAPS). This is the second post that covers configuration of Active Directory to support LAPS. For links to parts 1 and 3, see the bottom of this post.
Configuring Active Directory for LAPS
Extend the AD Schema
In the last post, we configured the client installation. While there is no server-side software to run as far as ensuring the system operates, there are a number of changes required to Active Directory in order to allow for secure password storage against a computer object. As part of this, we’ll be adding two attributes to Active Directory’s computer class:
- ms-MCS-AdmPwd - this attribute stores the password itself
- ms-MCS-AdmPwdExpirationTime - this attribute stores the time after which the computer’s password should be changed
In part 1, you would’ve installed the LAPS management tools onto a computer. Connect to this computer as a member of the Schema Admins Active Directory group. Open an elevated Windows PowerShell prompt and import the AdmPwd.PS module:
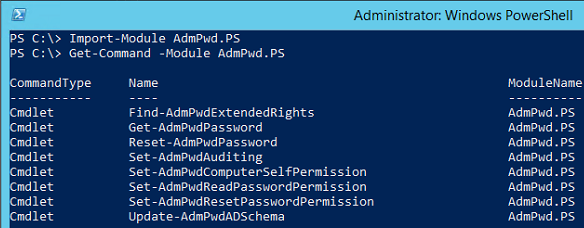
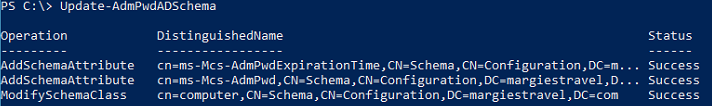
Once imported, you must extend the AD schema using the Update-AdmPwdADSchema cmdlet:
Configure Active Directory Permissions
By default, the vast majority of Active Directory computer object properties can be read by any user with Domain Users privileges or above. If we’re storing local administrator passwords, this isn’t necessarily a desired situation. Let’s dig into AD and restrict who can actually view this newly created ms-Mcs-AdmPwd attribute:
- Open ADSIEdit.msc
- Right click the ADSI Edit node and choose Connect to….
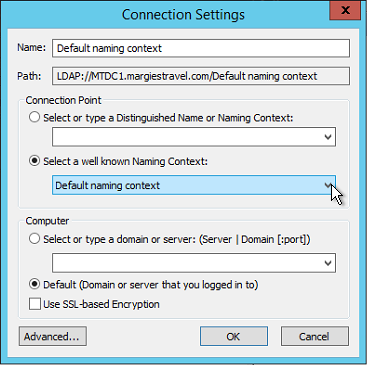
- Ensure Default naming context is selected and click OK
- Drill down the tree to find the organizational unit that contains your computer objects
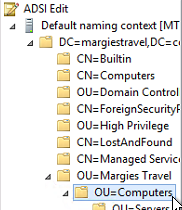
- Right click the OU and select Properties
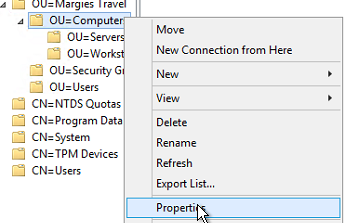
- On the Security tab, choose Advanced
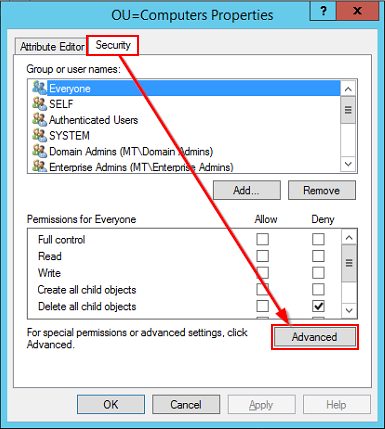
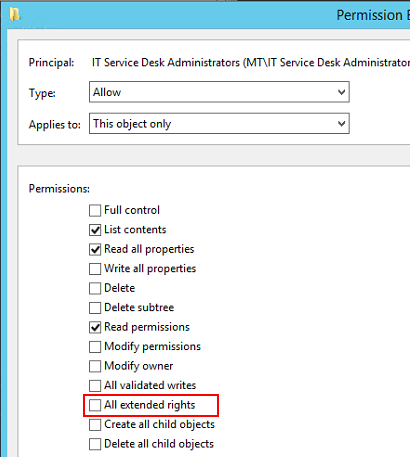
- For each non-administrative group that currently has it checked (if any), remove the All extended rights permission:
- Next, grant computers the ability to update their password attribute using
Set-AdmPwdComputerSelfPermission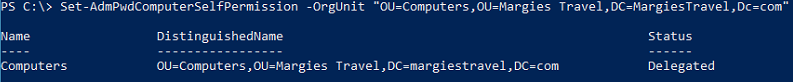
- Now it’s time to grant rights to users to allow them to retrieve a computer’s password. I’m going to use two different groups for this, one for servers and one for clients:
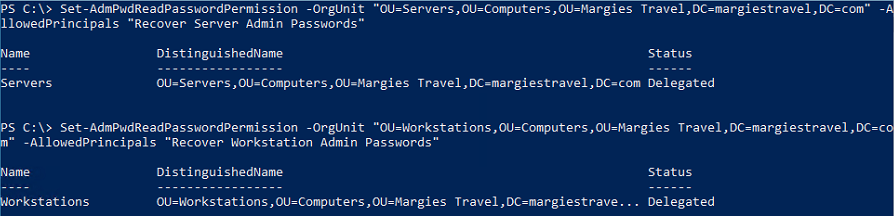
What Else?
Comments/questions
There's no commenting functionality here. If you'd like to comment, please either mention me (@[email protected]) on Mastodon or email me. I don't have any logging or analytics running on this website, so if you found something useful or interesting it would mean a lot to hear from you.