The PowerShell execution policy seems to be widely misunderstood. It is not there to stop administrators doing things. At all. This is why:
C:\> .\badscript.ps1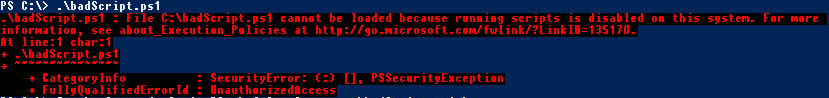
Cool! Can’t run the script! Right? Wrong.
C:\> Invoke-Expression (Get-Content .\badscript.ps1)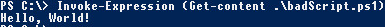
This is one of just many, many, ways to bypass the execution policy. So if you think this is all you need to do to protect your system from nefarious operators, now’s the time to rethink that. Execution Policy serves many good purposes, but stopping users of a computer from running commands is not one of them.
Comments/questions
There's no commenting functionality here. If you'd like to comment, please either mention me (@[email protected]) on Mastodon or email me. I don't have any logging or analytics running on this website, so if you found something useful or interesting it would mean a lot to hear from you.